
For a while now, I have been intrigued by the subject of information security. I encounter it both in my work and in my personal life, as do many others. Even people who have little or no involvement with it through their work are increasingly confronted with it. For some, it is an abstract, vague, and also grandiose subject. And, it seems to keep growing in size and application. I also see it more and more as a fun challenge to explain to “laypeople” what information security entails and why it is playing an increasingly important role.
The definition of information security
My challenge begins online. After all, there is an enormous amount of information available here. I found the following (complete) definition of information security: “the set of preventive, detective, corrective, and recovery measures, along with procedures and processes, that ensure the availability, integrity, and confidentiality (exclusivity) of all forms of information within an organisation or society, with the aim of ensuring the continuity of information and information provision and limiting the consequences of security incidents to an acceptable, predetermined level.” This is a fairly long sentence with a lot of information. I think this definition confirms the image that most people have of information security. Even people with some knowledge and experience in IT or risk management need to let this sentence sink in to fully understand what the definition entails. It is all the more fun to break down and make this definition tangible for everyone as an employee and as a citizen.
A two- or three-part series
This article focuses on what is meant by the availability, integrity, and confidentiality of all forms of information within an organisation or society. I won’t focus on what is meant by the set of preventive, detective, corrective, and recovery measures, as well as procedures and processes (for now). Maybe I can turn this in a two- or three part series in the future, who knows?
I’ll try to explain previously mentioned topics by using a lot of examples in attempt to make these concepts tangible. Before we dive into the explanation, it is important to visualise information security. Over the years, I have experienced it as a kind of matrix. Below you can see what it looks like to me.
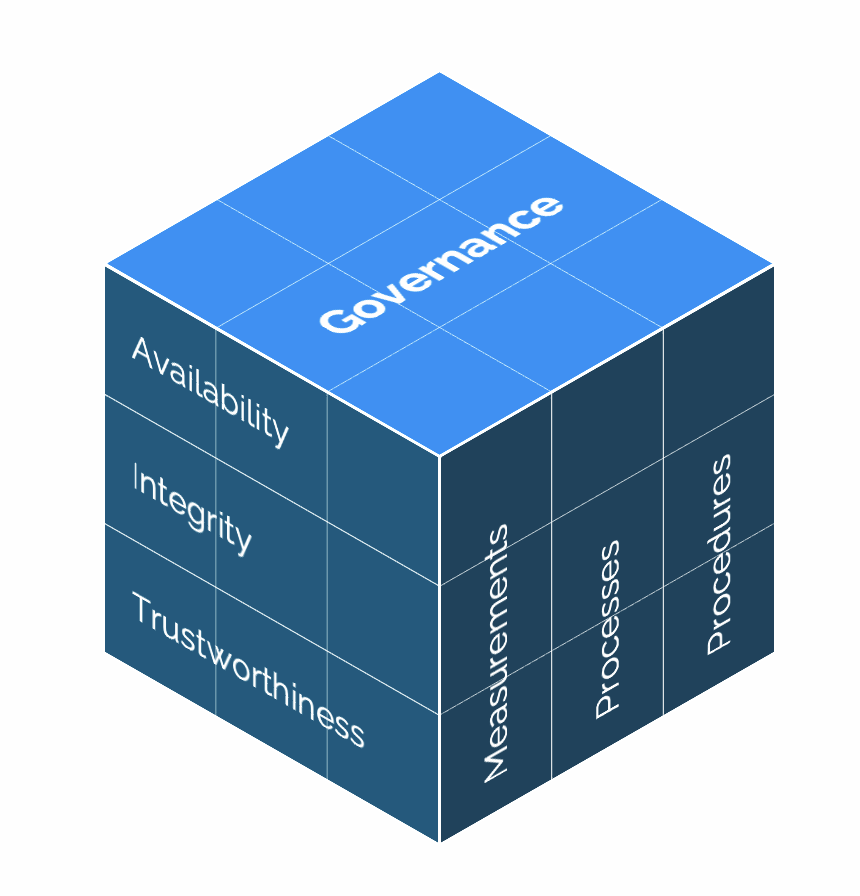
The importance of information
It has become clear to everyone that we live in a time where we generate (both personally and
professionally) a lot of information with everything we do, that organisations are collecting and using more data for various purposes, and that this also leads to more abuse of this data. In a nutshell, this is the main reason for the need to (better) secure information. We are slowly moving towards cybercrime, another interesting topic that has become more prominent due to the increasing amount of digitisation and digital storage of information.
So we are generating and using more information. Therefore, it is important that we:
- Have access to or can consult the information => availability
- Ensure that the information is up-to-date and accurate => integrity
- Ensure that the information can only be accessed by people who are authorised to see it => confidentiality
Organisations are collecting and using more data for various purposes, and that this also leads to more abuse of this data. In a nutshell, this is the main reason for the need to (better) secure information.
Availability
I think this topic is the easiest to understand and the one that is most appealing. As the name of the topic suggests, this topic is about the degree to which information is available. In other words, is it accessible (or available) when you want to use or access it? As an employee, you can think of being able to use or consult certain systems or finding information. Examples of this are the accessibility of Belastingdienst.nl when you want to file your annual tax return or being able to log in to any portal of an organisation of which you are a “customer.” Think of energy suppliers, healthcare institutions, telecom providers, pension funds, and especially your bank.
From these examples, I gather that we are mainly affected by not having access to the information (or service). This is what we logically remember, what may even make us nervous and what we complain about. And if something is not pleasant, both to receive and to do, then it’s somewhere to file a complaint. From this customer experience, it is also understandable that organisations or institutions analyse which information (or services) should always be available and take measures or establish processes for this.
Integrity
This topic is quite evocative, as in the Dutch language, it usually means reliability. In the context of information security, this topic means that information is up-to-date and correct. In other words, you can assume that the information you see is correct.
The most straightforward example of this for both employees and citizens is information in or from the Basic Registration of Persons (BRP). Various organisations or agencies in the Netherlands have a connection with this government register, which includes your address information, citizen service number, and data from a potential partner, among other things. When a change of address is made in the BRP, these organisations or agencies receive your new address as a modification. In most cases, this works well, but of course, mistakes do happen. I have moved a few times by now, and even after living at my current address for three years, I still occasionally receive mail from the previous occupant’s bank.

I play badminton for a club in the autumn competition. The badminton association assigns our (mixed) team to a regional pool of seven or eight teams each year, and then the clubs schedule the matches and report them to the association. The information about the competition matches is entered on toernooi.nl. Before the match, this information consists of the date and time of the match, the address of the sports hall, and the players who will participate in the match. After the match, the results are processed, and the outcomes of all played matches and the ranking within the pool are visible to everyone. In this example, availability and integrity come together. It is essential for a match that you can access information about the match, and that this information is correct. This prevents you from showing up at the wrong time or at the wrong sports hall. After the match, it is essential that the outcome is processed quickly and correctly, so that all teams in the pool know where they stand in the ranking.
Confidentiality
This topic focuses primarily on the privacy aspect of information and means that only those who are authorised to see the information have the possibility to access it. In recent years, this part of information security has been under scrutiny due to the introduction of the General Data Protection Regulation (GDPR) and the changing role of the supervisory authority, the Dutch Data Protection Authority. Almost every week, you can find a newspaper headline about a data breach. Something is a data breach if personal data that was not intended for someone has been shared with that person or was available in some way. The latter happens on a large scale online with databases, including those obtained through hacks. The former occurs on a smaller scale, and you can think of the bank post I received, which was actually meant for the previous residents of my house.
Going back to my example of the badminton club, I filled in my details on the registration form when I joined. The club may (from me) have the information it needs to carry out the membership administration and to exchange the necessary information with the badminton association. The badminton club sends a monthly newsletter digitally, with all email addresses included in the BCC so that another member of the club cannot retrieve my email address via the newsletter. Where in the past, the address and telephone number were available for everyone to look up in the phone book (remember that?), we now do not find it very pleasant if people we do not know retrieve our address. What I mean to say here is that the board members may, of course, have the information I have provided for my membership, but it should also stay with them.
The BIV classification
Information security consists of three topics: availability, integrity, and confidentiality. Within many (IT) companies, the BIV score or BIV classification is discussed, which is an abbreviation of the first letters of the three topics. Based on risk analyses, each system that an organisation uses and/or a group of information is assigned a score from 1 to 4 per letter on a scale of 1 to 4. 1 being the lowest level and 4 being the highest. This indicates what the desired security level for this system or information is. The figures for the topics are described in the figure below.
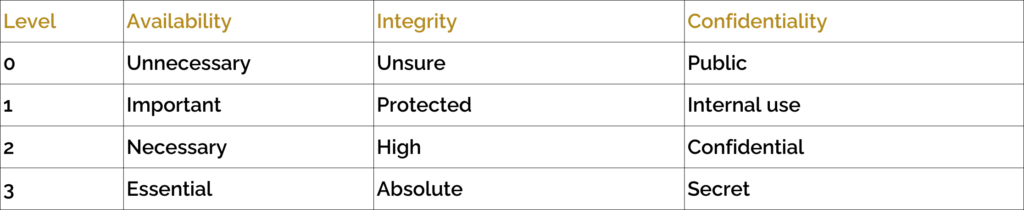
We can use online access to our banking data as an example to understand how the BIV classification works. In nearly all cases, banking data needs to be available, both for individuals and certainly for organisations/entrepreneurs. Therefore, we assign the number 3 to the B in this example. When we access our banking data, it’s preferable to have the most up-to-date information, although most of us find it acceptable if transactions are not processed immediately during evenings and weekends. Therefore, we assign the number 3 to integrity in this example. Finally, we consider it unacceptable for anyone other than ourselves (or an authorised person) to have access to our banking data. Therefore, we assign the number 3 to confidentiality. This leads to a BIV classification for our banking data of 3-3-3. The BIV classification largely determines how much effort (think of money and attention) is required to secure the information. In other words, what measures are taken, what processes are set up, what procedures are applied, and which standards are met.
Laws and regulations and standards
Over the years, various national and international laws have come into force that affect information security. Guidelines and standards for information security have been developed, such as the ISO 27000 series (international) and the NEN 7500 series (Netherlands), partly as a result of this. If an organisation or institution is certified to one of these standards, it serves as evidence that the organisation has the necessary measures, processes, and procedures to secure the information.
The whole of laws and regulations, standards, measures, processes, and procedures is so comprehensive and interesting that it deserves its own article. Make sure to follow the Projective Group page if you want to stay in the loop.
About Projective Group
Established in 2006, Projective Group is a leading Financial Services change specialist. With deep expertise across practices in Data, Payments, Transformation and Risk & Compliance.
We are recognised within the industry as a complete solutions provider, partnering with clients in Financial Services to provide resolutions that are both holistic and pragmatic. We have evolved to become a trusted partner for companies that want to thrive and prosper in an ever-changing Financial Services landscape.



