
As discussed in our previous articles on the Digital Operation Resilience Act (DORA), this new regulation imposes all sorts of requirements on the internal organisation of financial institutions. These include ICT roles and responsibilities, the establishment of ICT risk management and ICT incident management. In addition, there are rules for the use of third-party ICT providers.
Table of Contents
Managing ICT third-party risk
Various legal frameworks already existed for this purpose, such as the ESMA Cloud Outsourcing guidelines or the EBA guidelines on outsourcing. DORA brings these requirements, and sometimes even more, together in one chapter. In this article, we dive further into Chapter V of DORA: Managing of ICT third-party risk. Article 28 to 44 DORA describe these rules with associated RTSs providing further details.
In short, managing the ICT third-party risk comes down to a combination of risk management and vendor management. When concluding an ICT contract, it is important to identify the risks in advance. It is also important to have a well-defined process in place to select new suppliers in a consistent and compliant way, and to monitor the service levels during the contract period. DORA sets specific requirements for these different phases in the process.
General principles (art. 28 DORA)
At first glance, the chapter starts with the general principles for sound ICT risk management of third-party providers. But when you read the article, it turns out to contain quite specific requirements.
A key principle is that financial institutions themselves remain responsible for complying with DORA obligations. In short: the rules that apply to the institution itself also apply when a process or part thereof is performed by a third party. This is already the case under current legislation, and is also emphasised in DORA.
Often, ICT management will be provided by a third party. After all, for many financial institutions, ICT management is not their core business. But this does not exempt the institution from complying with the rules and the obligation to check whether these third parties comply. For this reason, ICT third-party risk from third-party providers should be part of the ICT risk management framework. A ‘strategy on ICT third-party risk should be established (and regularly reviewed). In this strategy, you can explain the method chosen. Is much left to third parties or not, and why? And how will the process be managed?
A key principle is that financial institutions themselves remain responsible for complying with the DORA obligations.
The principle of proportionality may be taken into account when managing third-party providers (see Article 28(1)(b) DORA). It therefore matters how large and complex the service is and whether it is critical to the operation of the business.
Microenterprises, including small and non-interconnected investment firms* , are not required to have a third-party ICT risk strategy in place. The other requirements do apply to them.
In addition to having an ICT risk strategy for third-party providers, the following requirements apply:
- The presence of a register of information relating to all contractual arrangements;
- A reporting obligation to competent authorities on new arrangements on the use of ICT services;
- A selection process that takes into account supervisory conditions, identifying relevant risks and conducting due diligence;
- An assessment of the presence of various mandatory contract requirements; and
- A (tested and evaluated) exit plan for ICT services that support critical or important functions.
We elaborate on these commitments in the following paragraphs.
For which ICT services do these requirements apply?
Before looking further into the obligations, it is good to consider what is meant with ICT services. The definitions of the Act (article 3 subsections 18-22 DORA) explain the terms:
- ICT third-party risk: means an ICT risk that may arise for a financial entity in relation to its use of ICT services provided by ICT third-party service providers or by subcontractors of the latter, including through outsourcing arrangements;
- ICT third-party provider: an undertaking providing ICT services.
- ICT services: digital and data services provided through ICT systems to one or more internal or external users on an ongoing basis, including hardware as a service and hardware services which includes the provision of technical support via software or firmware updates by the hardware provider, excluding traditional analogue telephone services;
- Critical or important function: a function, the disruption of which would materially impair the financial performance of a financial entity, or the soundness or continuity of its services and activities, or the discontinued, defective or failed performance of that function would materially impair the continuing compliance of a financial entity with the conditions and obligations of its authorisation, or with its other obligations under applicable financial services law;
In terms of a financial institution’s business operations, this means that all agreements with external parties relating to ICT systems fall under this definition. This includes software, hardware, but also e.g. data center usage. For instance CRM software, laptop management, portfolio management software, Microsoft 365 etc. If the institution is part of a group, and another group part provides the ICT services, this is also treated as an agreement with a third party.
What does this mean for existing ICT contracts?
Now that we know which contracts are covered by the regulations, the question is of course how these contracts will be affected. The new rules taking effect from January 2025 will apply not only to new ICT contracts but also to those already in place. This means that in the run-up to DORA coming into force, financial institutions will have to scrutinise their existing contracts and adjust them where necessary.
Whereas implementation for the other obligations is mainly an internal matter for a financial institution, here it also requires cooperation of the third party; the supplier. The more contracts there are, the greater the impact. Possibly this makes it one of the most time-consuming jobs of the DORA implementation.
DORA imposes requirements on contracts, with additional obligations for critical or important contracts. These requirements are not all new, so for some contracts the impact will be limited. DORA describes:
- What to consider when concluding new contracts;
- Which topics should be part of the contract;
- How contracts should be recorded.
New ICT contracts in line with DORA
When signing a new contract, for example, the following points must be taken into account:
- It should be assessed whether the function is critical or important, whether the supervisory conditions are part of the contract and whether there may be a conflict of interest.
- Risk assessment and due diligence must be carried out, see Art 28(4) DORA.
- Also, when contracting for critical or important functions, it should be determined how dependent the institution becomes on the third party, and how easily the third party can be replaced (Art. 29 DORA).
- Finally, the third party must have an appropriate level of information security.
Before a financial institution selects a new partner, it is therefore important to thoroughly consider the potential risks and weigh them up carefully. A good process and record keeping is important here, if only because newly concluded ICT contracts must be reported annually to the regulator (Art. 28(3) DORA).
Contractual provisions
Besides the requirements applicable to the selection process, there are also contractual provisions that must be part of the contract. For instance, a number of situations are named in which the contract must be terminable (Art. 28(7) DORA), along with requirements for the termination process for critical and important contracts.
Article 30 of DORA also lists some essential contractual provisions, including a detailed description of services, availability, incident management, audit rights and outsourcing conditions. Paragraph 3 of this article provides additional requirements for contracts with parties supporting critical or important functions. All in all, the requirements for the latter category logically, are a bit strikter than for regular contracts.
Record of contracts
Contracts should be in writing and contain the rights and obligations of both parties. There should be one written document that contains the service level, the Service Level Agreement (SLA), in addition to the contract. There should also be a record of all contracts in the register of information.
An ITS has been published that further describes this obligation. Next to that, a sample register was published that can be used, and adapted to the institution’s risk profile. Supervisors can request all or part of this register for inspection, with associated necessary information (Art. 28(3) DORA).
Supervision of ‘critical providers’
Finally, the legislator has included a clever feature in DORA that ensures that not only financial entities become more resilient, but also their providers. This is described in Article 31 DORA. Whereas the regulator normally only focuses on licensed financial entities, it will now also focus on critical providers.
The ICT third-party providers that are considered critical to the sector will be designated by the ESA’s. This list will be published, when this will happen is unknown yet.. A “lead overseer” will be established to supervise those parties at European level. Probably the list will consist of, the ICT third-party providers that, for example, support the largest banks and on which there is a high dependence for the financial system.
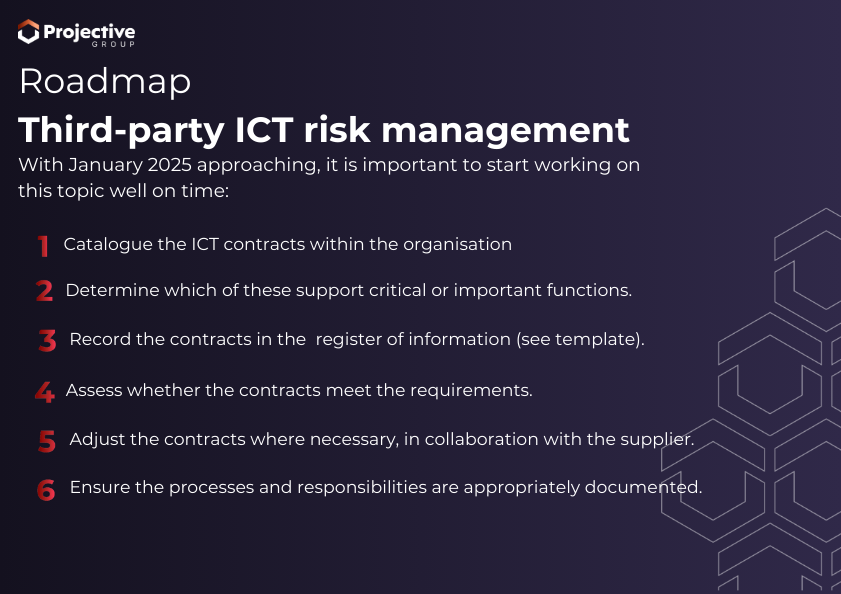
Roadmap for third-party ICT risk management
With January 2025 approaching, it is important to start working on this issue in good time. Especially if a review of existing contracts has yet to take place. One possible approach could be:
Want to know more?
Do you have questions about implementing DORA requirements within your organisation, or could use some help reviewing existing contracts? If so, please contact us without obligation.
If you would like to keep up to date with developments at DORA, you can subscribe to our monthly Risk & Compliance newsletter.
* For the full definition of micro-enterprise, see Article 3(60) DORA, and further exceptions see Article 16(1) DORA.





